TCP Monitor
Written by Clifford
Using the TCP monitor in Anturis Console, you can set up monitoring of general availability and response time for any service running on a server connected to the internet. It also enables you to set up a notification when a certificate for a secure TLS/SSL connection is about to expire. You can send requests either from one of the components in your infrastructure, or use one of the available Public Agents that are maintained by Anturis in different geographical locations.
Transmission Control Protocol (TCP) is used along with the Internet Protocol (IP) to send data between computers connected to a network. Together, they form the Internet protocol suite, also known as TCP/IP. In this model, the TCP layer is responsible for dividing a message from an application program into packets, numbering the packets, and forwarding them to the IP layer that handles the actual delivery. On the destination computer, TCP reassembles the packets and forwards the message to the intended target application. So, while actual delivery is carried out by the IP layer, TCP is responsible for error-checking and controlling the order of a data stream.
This model works for most types of data in any network, because other protocols are designed within the framework of TCP/IP. For example, web browsers use HTTP on top of TCP for communication with web servers. The same is true for SMTP, POP3, and IMAP in the case of communication between mail clients and servers.
For secure communication, TCP is layered on top of the Transport Layer Security (TLS) protocol, which was previously known as Secure Socket Layer (SSL). TLS/SSL are cryptographic protocols for secure communication over computer networks. They are based on the exchange of X.509 certificates and public keys for encrypting and decrypting messages. Digital certificates are issued by a certificate authority (CA) trusted by both parties involved in the communication. A certificate binds the public key to a person or organization for a predetermined period of time (until the certificate expires).
As a transport layer protocol, TCP uses ports, which are application-specific endpoints in network communication. When added to an IP address, the port number completes the address for a TCP/IP connection. Port numbers are bound to specific processes on the destination computer. Port numbers are 16-bit unsigned integers ranging from 1 to 65535. Some well-known ports are reserved for the most common services. For example, an HTTP service application (like a web server) listens on port 80, while an FTP service is bound to port 20 for data transfer and port 21 for commands. You should not use any of the well-known ports (0 to 1023) or ports registered by companies and other users (1024 to 49151) for custom or private purposes.
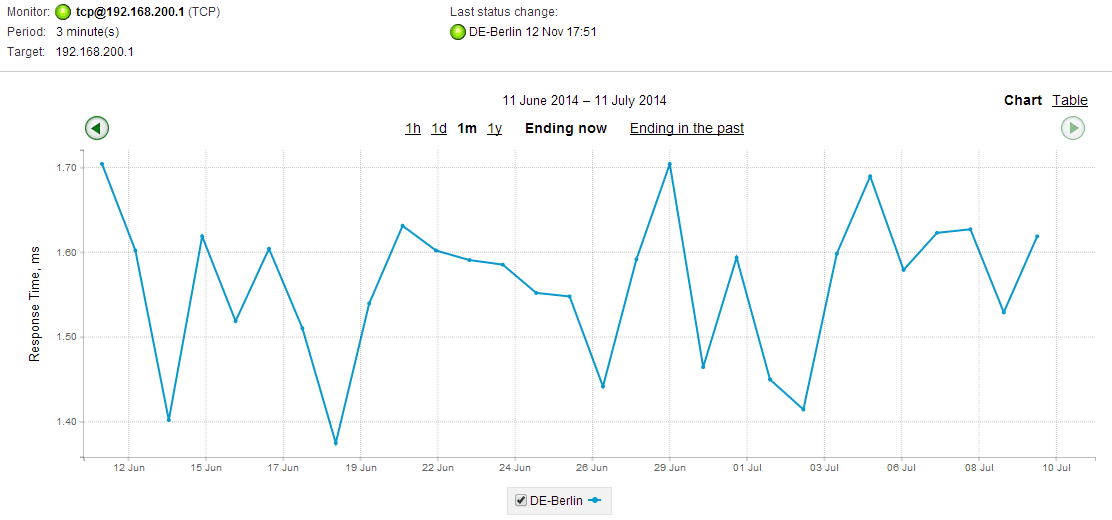
By sending regular requests to a TCP port, you can track the time it takes for a response to return (also known as round-trip delay time, latency, or timeout). This helps you monitor both the reachability and the performance of your critical network services. Long timeouts can greatly affect the quality of services you provide to your customers. For example, you may want to monitor the availability of your Microsoft System Center Operations Manager (SCOM) server on port 5723, and make sure that responses are not delayed. The sooner you are able to detect a possible issue, the faster you will be able to react to it. If the server uses TLS/SSL security, it is also important to monitor the certificate expiration date.

Leave a Comment