SSH Monitor
Written by Clifford
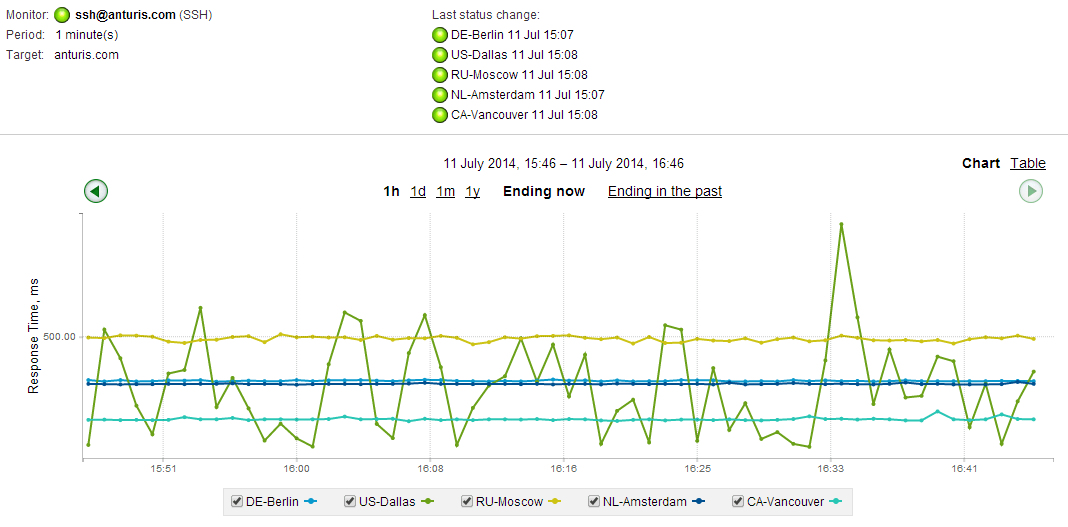
Using the SSH monitor in Anturis Console, you can set up monitoring of general availability and response time for any remote SSH server connected to the internet. You can send requests either from one of the components in your infrastructure, or use one of the available Public Agents that are maintained by Anturis in different geographical locations.
Secure Shell (SSH) is a cryptographic protocol for secure access to a remote computer over an unsecured network. Besides logging into a computer and executing commands, it can be used for secure file transfer between computers, forwarding, tunneling a port to a remote computer, and so on.
When you need to perform management tasks on a remote server, SSH is the best solution, because it does not require physical access to a server that may be thousands of miles away. Both SSH clients and daemons are available by default on most modern operating systems, including Mac OS X, Solaris, and various BSD and Linux distributions. Windows does not include SSH support by default, but a lot of third party software exists.
The default port number that an SSH server listens on is 22. SSH connection and authentication is carried out using public-key cryptography. You can use a public-private key pair automatically to encrypt the connection and then authenticate with a password. Or you can generate the key pair manually to use it for authentication instead of a password. This makes the client authentication layer in SSH highly extensible and very different from the Transport Layer Security (TLS) protocol, which was previously known as Secure Socket Layer (SSL). The transport layer of SSH handles the initial key exchange and is comparable to TLS/SSL. The connection layer in SSH is responsible for creating a secure channel between a server and a client computer over an unsecured network.
By regularly sending SSH requests and tracking the time it takes for a response to return (also known as round-trip delay time, latency, or timeout), you can ensure that those servers that are critical for you are available for remote SSH access. This directly affects your ability to perform remote management on the server. The sooner you are able to detect a possible issue, the faster you will be able to react to it. Without SSH, or if SSH requests are too slow, when the time comes to configure your server, you will be forced to access the server physically, which may take a lot more time than a remote login.

Leave a Comment