11 Awesome Tools for Linux SysAdmins
Written by Clifford
Here we look at some cool tools that the Linux system administrator will find useful or even indispensable. The tools we’ll discuss in this article are all free.
Puppet Open Source
Puppet is available in both a free open source version and a paid commercial version known as Puppet Enterprise, which includes extra features and support. Puppet is used for IT automation, orchestration and reporting. With Puppet, you can define the desired state of your system, simulate the changes before implementing them, enforce and deploy the desired state automatically, and then report the differences between the two states of before and after Puppet has run and enforced the desired state. The desired state is defined on the Puppet master, and your Puppet agents will be installed on those servers that you want to control: the agents will get the desired state from the master and then implement it.
To understand better how this works here are some examples of what Puppet is capable of doing; in each example imagine that you have hundreds of servers that you manage.
- Control files: Linux is based around files; by modifying files you can control almost everything. Rather than editing files on different servers in the way that you require, you can specify this on the puppet master. The puppet agents will ensure that the same file is present on the server where it is installed. For example, you have a custom /etc/ssh/sshd_config and /etc/sudoers file that locks down SSH and gives root access to admins. You can roll out these files automatically and any future changes with Puppet. If someone such as an attacker changes or overwrites any of the Puppet controlled files the desired changes will be put back.
- Set cron jobs: Puppet can set cron jobs on a server from the Puppet master on all of your servers, so you can schedule jobs anywhere without having to manually set these up.
- Install or remove packages: You can ensure that packages are installed or removed from your servers. For instance, if you need Apache you can ensure that it’s always there along with the required configuration files that you have set. Alternatively, if you want to ensure that Apache is removed you can set this as well, if someone installs Apache then Puppet will remove it.
- Ensure services are running: Puppet can check to ensure that services are running or stopped. For example, you can ensure that Apache is always up and running. If Puppet detects that Apache is not running it can try to start the service.
- Execute commands: You can also set Puppet to run a command on all of your servers. So, you could use Puppet to run the auto install command for the Anturis agent to have it installed automatically on all of your servers that you wish to monitor, saving a lot of time.
It’s important to note that the above only happen when the Puppet agent completes a run. When this happens it will get the desired configuration from the Puppet master. By default the Puppet run will happen every 30 minutes. However, you can change this time.
Puppet MCollective
MCollective is a framework to build server orchestration or parallel job execution systems. The service is separate to the puppet agent but typically installed with it. It can scan your network for virtual machines based on command-line criteria.
Then it lets you send them messages – for example, to find out which ones are down, or to restart the processes on the machine or the whole machine from one central location. The application is written in Ruby, so you could copy some of that and adapt it to your specific needs.
The data comes from Puppet, Chef, Facter, and other plugins. It reads the metadata left behind when you used those tools to build the machines.
Here are some example MCollective commands and a list of what you can do with the tool:
- mc-find-hosts: finds all virtual machines.
- mc-facts shows which machines are located in what countries.
- mc-service –with-class /dev_server/ httpd status: finds machines that are running web servers.
- use mc-rpc to send messages to machines and discover those with errors when they do not echo back the same message.
- mc-service –with-class /dev_server/ httpd restart: restarts development web servers.
Webmin
Webmin is an open source tool for managing server configuration; it allows you to administer your server through a web interface via a browser rather than working directly with files through SSH, for example. You can use it to set up user accounts, disk quotas and Apache config files, and to create user accounts, enable file sharing – and more.
The system is configured using administrative modules, which are .gz module files and can be added to increase functionality and implement updates. Below are some example modules that are available. There are plenty more that can be downloaded.
- Apache – configure almost all Apache directives, which is a lot easier than typing them by hand
- Bind DNS Server
- BSDS Firewall
- Backup Configuration Files
- Change Password
- CD Burner
- DHCP Server
- File Manager
- File System Backup
- Kerberos
- LDAP Client – search and edit LDAP records
- LDAP Server – manage OpenLDAP
- Network Configuration
Darik’s Book and Nuke
This is a free tool used to erase data from all disks on a server. It’s a boot disk that will erase any disks that can be detected making it useful during the server decommissioning process. Be careful where you use it! It works with Windows and Linux and is useful when you need to ensure that data has been securely erased so that it cannot be recovered – so be sure that you really want to remove the data stored on the disks on the server you mount the ISO to.
Wireshark
Wireshark is a network protocol analyzer, also known as a network sniffer. It’s similar to other tools such as tcpdump but with a graphical interface and the ability to more easily filter traffic by type, source and destination addresses and ports. Wireshark can run on all of the popular operating systems, it uses libpcap on Linux to capture packets and WinPcap on Windows. You can use it to troubleshoot network and application issues or simply to monitor what traffic there is on the network.
On a security issue note, any snoop tool can only sniff packets going to and from your machine. To change that you would have to set up your router in promiscuous mode or plug your machine into a hub, router, or switch in your network.
On a busy network the output from Wireshark will go by on the screen very fast. You can log the traffic into a .pcap file for review at a later time.
Ubuntu Rescue Remix
This is a custom live CD of Ubuntu Linux used for data recovery and forensics. You can boot it with a USB drive or CD and then inspect disks at the block level, meaning that it can work on any operating system’s file system, such as Windows or Linux. Once booted you will be provided with a Linux shell and various tools to help with data recovery, it includes ddrutility for instance, which shows file fragments and names in unrecoverable disk blocks. It also includes many other useful data recovery tools such as PhotoRec, The Sleutch Kit, Gnu-fdisk, and ClamAV which can be useful for scanning for malware and viruses.
The project is currently no longer supported or maintained by the developer. However, it still works great. If it does what you need then you shouldn’t have any problems. If not, don’t bother to write for support until someone else takes over the project’s source code. As it has been around for a while you probably won’t find any problems or limitations that you cannot work around.
TightVNC
TightVNC provides remote access to a graphical user interface (GUI) allowing you to control a Linux system without actually being at the machine. Typically, Linux servers are administered over command line with SSH, however some users will prefer to manage the server with the GUI, especially if it is a desktop machine. VNC works in a similar way to Microsoft’s remote desktop application; you just need to install and run the VNC server onto the machine you want to connect to. Once configured, you will be able to connect remotely.
Something to be aware of is that VNC is not secure. Traffic is transferred over the network in plain text or in a way that can be cracked, so connecting to VNC with a username and password, for instance, is generally not secure by default; this information can be obtained using a tool such as Wireshark. To increase security most VNC clients will allow you to tunnel VNC over SSH. This is secure as SSH is used to establish an encrypted connection to the machine to which you can then connect with VNC over the top.
There are VNC clients available for Windows/Linux/Mac OS X so you can connect from almost anywhere. There are even Android clients as well so you can connect from a mobile device, and one of the most popular ones currently is ‘Ripple’. VNC is platform-independent so there are many different versions around that you can use, such as TigerVNC, TightVNC and RealVNC.
ConfigServer and Security Firewall
CSF is a suite of scripts which provide firewall, login, intrusion detection, and more. The firewall is essentially a front end to iptables with plenty of additional useful features. Firstly, it uses the iptables firewall, allowing you to implement rules without needing to understand the details and syntax of iptables. This allows you to secure your server by locking down both inbound and outbound traffic. For instance you can set up your server to only allow SSH connections on port 22 from 192.168.0.1 and to deny all other requests to port 22.
CSF is also able to actively block attacks. So, if you are allowing 192.168.0.1 into port 22 and someone compromises that server, if they then try to SSH into your server, despite being allowed in the firewall, if they fail to log in a set amount of times within a set period of time, their source IP address will be blocked in the firewall temporarily. If enough temporary blocks occur they can be blocked permanently as an attacker. This works for a lot more than just SSH, it also works for failed logins to web pages protected with htpasswd, Exim SMTP authentication, Mod_Security failures, or even FTP from vsftpd/proftpd/pure-ftpd.
While CSF can be used on a standalone Linux server, it has a GUI component if used on a WHM/cPanel server. It can be configured and managed via WHM, rather than through the command line, which is great as WHM hosting is very popular.
Capistrano
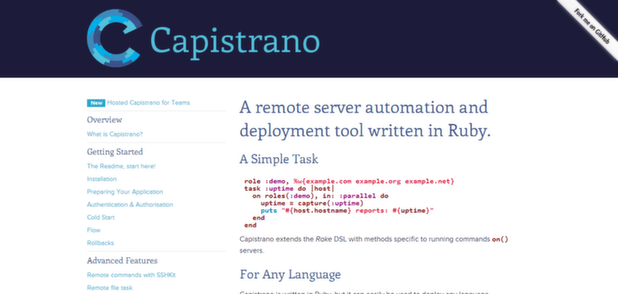
Capistrano is an open source tool written in Ruby for remote server automation and deployment. It supports scripting and execution of tasks, and can be used to deploy web applications to multiple machines simultaneously or in sequence, perform data migration, run automatic audits (checking logs, applying patches, etc), and to execute other tasks. You can add other source control management software into Capistrano to expand its capabilities.
Capistrano is a Ruby gem, meaning it gives you complex functionality that you can use in a simple manner, as explained here.
Fabric
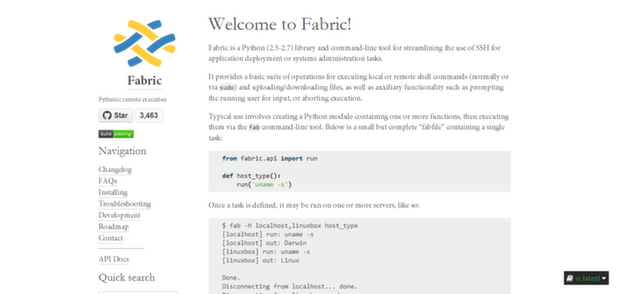
Fabric is a Python library and command line tool that streamlines the use of SSH for application development or administration tasks. It provides operations for executing local or remote shell commands. You create a module containing one or more functions, then execute them via the fab command line tool.
Once this task is defined, you can run it on multiple servers. For instance, run “fab –H localhost,remoteserver host_type” and you will get the output of ‘uname –s’ from all specified servers, in this case from localhost and remoteserver.
You only have to define a module once: you then invoke it by typing that name at the command line. As you can see, this functionality can be quite powerful.
MySQL Tuner
MySQL Tuner is a Perl script which can be used to quickly examine MySQL on your server and to provide suggestions to increase performance and stability.
While the advice provided by the script is generally good, only put changes in that you understand and know what they are actually doing. If you look up the MySQL documentation for the various variables it should explain to you how they work. Basically, you should perform changes on a test server if possible and not straight onto a production server; some changes will require a MySQL restart, potentially leading to downtime. Poorly set variables can also reduce performance and stability.

Leave a Comment