How the Tor Network Works
Written by Clifford
When Edward Snowden wants to chat with journalists, and not be spied on, he uses Tor (‘The Onion Router’) network.
Tor hides the sender’s IP address, protecting their identity by bouncing their communications across different nodes in the Tor network, only one of which knows where the data came from.
Tor is Secure, because no one Controls it
Tor is an encrypted network of computers operating under the control of no single entity. The software is maintained by the Tor open-source project, meaning anyone can obtain the source code to see how it works and verify that is has no backdoor to defeat its privacy. It is ironic that Tor was developed by the US military, and that 60% of its funding comes from them, because it is the US military (who runs the NSA) that has been especially busy trying to hack into it. Documents leaked by Edward Snowden say they have not been able to do it. The US government uses Tor itself when its employees travel overseas.
Because Tor is not run by any single organization, no one can be coerced into handing over its encryption keys to the NSA, law enforcement, or any other espionage or law enforcement agency. The software operates much as Bitcoin does, meaning people volunteer their computers to operate as nodes in the network. Even if the NSA were to set up their own Tor nodes—and one can reasonably assume they have – they could not read the source IP address passing through their node.
How it Works
The reason the Tor network can protect your identity is that the source and destination IP addresses are not stored in the data. Instead, Tor only stores the destination address and the IP address of the node that last processed the data. You can see this if you run Tor and then connect to the website whatsmyip.com; it will show a blank instead of your IP. Google too will ask you to type in a catch phrase when you use Tor, telling you there is something wrong with your internet signal.
Normal internet traffic, even if it is encrypted, like VPN, only encrypts the data part of the packet. The source and destination IP addresses remain visible. This means someone intercepting this traffic can read from where it is going and from where it is sent. If you are Edward Snowden talking to The Guardian newspaper, your privacy could be compromised.
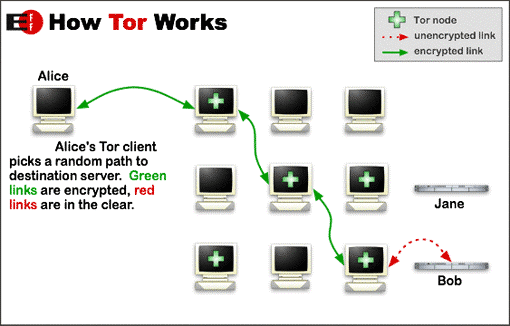
Tor Network. Courtesy of www.torproject.org
Tor works by encrypting the destination IP address. The source IP address is not stored, only the IP address of the last node used in the Tor network. So, someone could not tell where the data came from, even if they could defeat the encryption. For example, if I send something to you, any relay in the Tor network knows only that the data is going to you. It does not know where the data is coming from. Data that you send back to me, in the case of someone using encrypted chat, would protect your identity in the same manner.
There are thousands of Tor relays in operation. When Tor sends data, it randomly picks which relay to use to receive the next hop. That relay then picks the next relay and so on. Each relay exchanges encryption keys with the adjacent relay so that communication between the two relays can only be read by those two relays. It’s like one of those spy movies, in which the spy keeps changing cars so they cannot be tailed, except the driver does not know where the passenger is coming from, only where he is going. For a spy, whose driver is captured, that could be a bad thing.
Picture of Actual Tor Node Showing Traffic Stats
Weaknesses and Strengths
There are some weaknesses in the Tor network, such as the exit and entry points. By definition traffic going to the first hop in the Tor network would not be protected by Tor-type IP address encryption. The exit point has the same issue. You cannot send encrypted traffic to a website that does not except it, except, of course, SSL, but Tor is not SSL. You cannot send email to an SMTP server that does not support TLS: not many do. But there are websites that are configured to handle encrypted traffic from Tor. These are called hidden services.
A further weakness with Tor is that it is possible to track down both ends of Tor communication using correlation. That means using statistics and a very powerful computer to look at internet traffic and match up who is talking to whom based upon the timing of such communications.
What about the actual RSA encryption algorithm used to encrypt the data? Is that secure? This encryption is based on a 2,000 year math problem that no one has solved, which is how to factor a prime number without trial and error guessing. That can take years, if the encryption key is large enough.
Tor uses SOCKS, which means a proxy server. You can use it with any program that supports SOCKS, like Torchat, which enables encrypted chat communications. Browsers support SOCKS, but the user needs to know how to configure the proxy server IP and port number, as Tor runs on the PC or mobile device as a proxy server. To eliminate the need to configure this yourself, and to configure additional security measures, Tor recommends that you download their own browser.
When you download the Tor app onto an Android device, Tor can encrypt all internet traffic that supports encryption. But it requires that you have rooted your phone, meaning that you have bypassed Android security to give applications root access to the device. This way you do not need to configure your browser to use Tor.
To summarize, Tor is a useful tool for those who need something more secure than VPN. VPN is hosted by one company and could thus be compromised by subpoena, although some VPN services, like NordVPN, offer a miniature two-relay version of Tor, to make that less likely. Tor runs slower than VPN or SSL, since there are different relays to navigate, but it is not that much slower.
If you want to surf the web and frustrate those who might spy on you, Tor is a guaranteed safe way to do it.

Leave a Comment